Category: Security
-
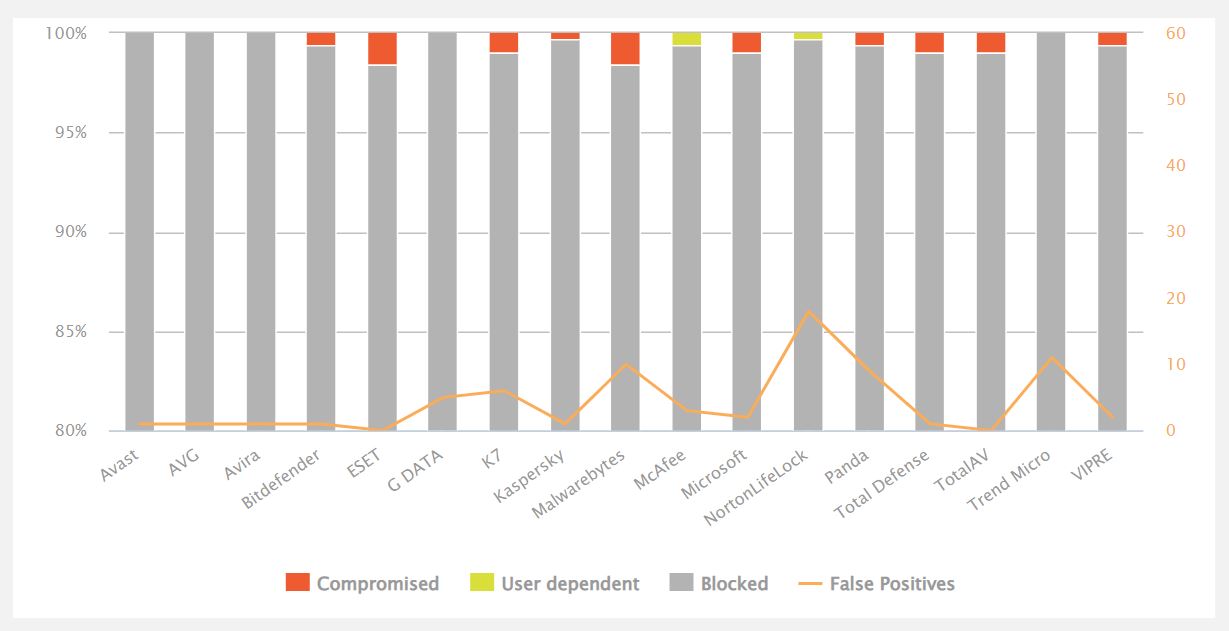
Moving on from Bitdefender: Avira, AVG or Avast?
I’ve recommended Bitdefender Free Anti-Virus countless times. It consistently received the highest scores in AV-Comparatives’ Real-World Protection Tests. Better yet, it just sat in the background doing its job: no needless popups, no scare tactics to ‘persuade’ you to upgrade. But last December it was withdrawn so I switched to Bitdefender’s paid Total Security. While I’ve been…
-
2FA: what’s it all about?
One of IT’s biggest barriers is jargon, where simple concepts are given overly complex names. Among those is 2FA (two-factor authentication) or MFA (multi-factor authentication). Why don’t they just call it “Another way of checking that you really are who you say you are”. OK, maybe that’s a little wordy! Remember how easy it was…
-
Password managers
How do you deal with passwords? Do you use the same one for every account? [Please, please don’t do this!] Do you write them down in a notebook? [Better; two cross-referenced notebooks are better yet.] Do you reset the password each time you log in to an account? [That’s actually really safe, but such a…
-
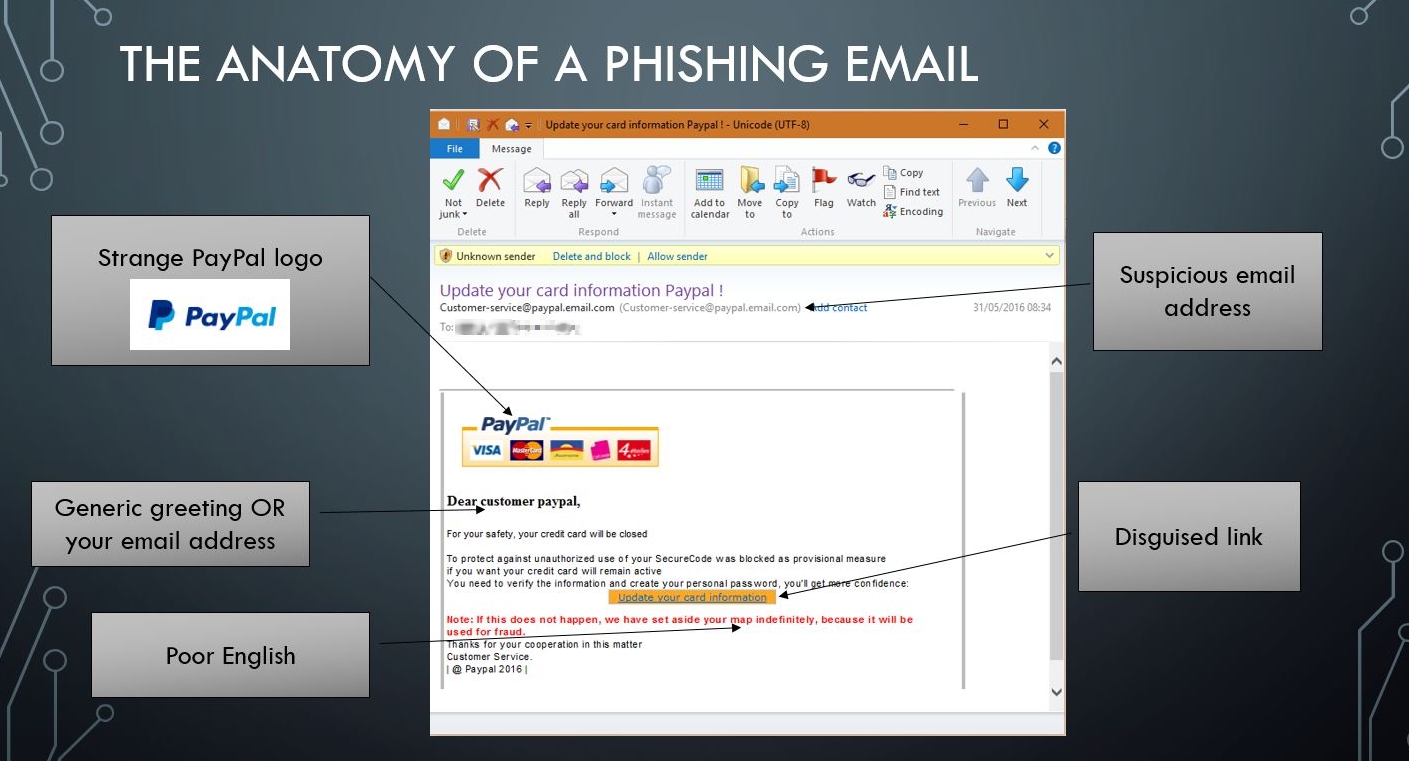
If you suspect deceit, hit delete!
Recently, someone in Jakarta changed the details of my Paypal account. Adaline Alexander from Alabama purchased three songs on my iTunes account. And in a moment of madness, I bought an $800 Dell laptop for Loretta Lestrange from New York. Of course, none of these things actually happened. But someone wanted me to believe that…
-

Is that a fact?
In 2009, when my Dad forwarded this chain email to me I replied, “Thanks for the heads up, but actually, this is a hoax … see this article on Snopes. It’s always worth checking on Snopes – a site which exists to debunk urban myths and other such things – before forwarding them on.” But…
-
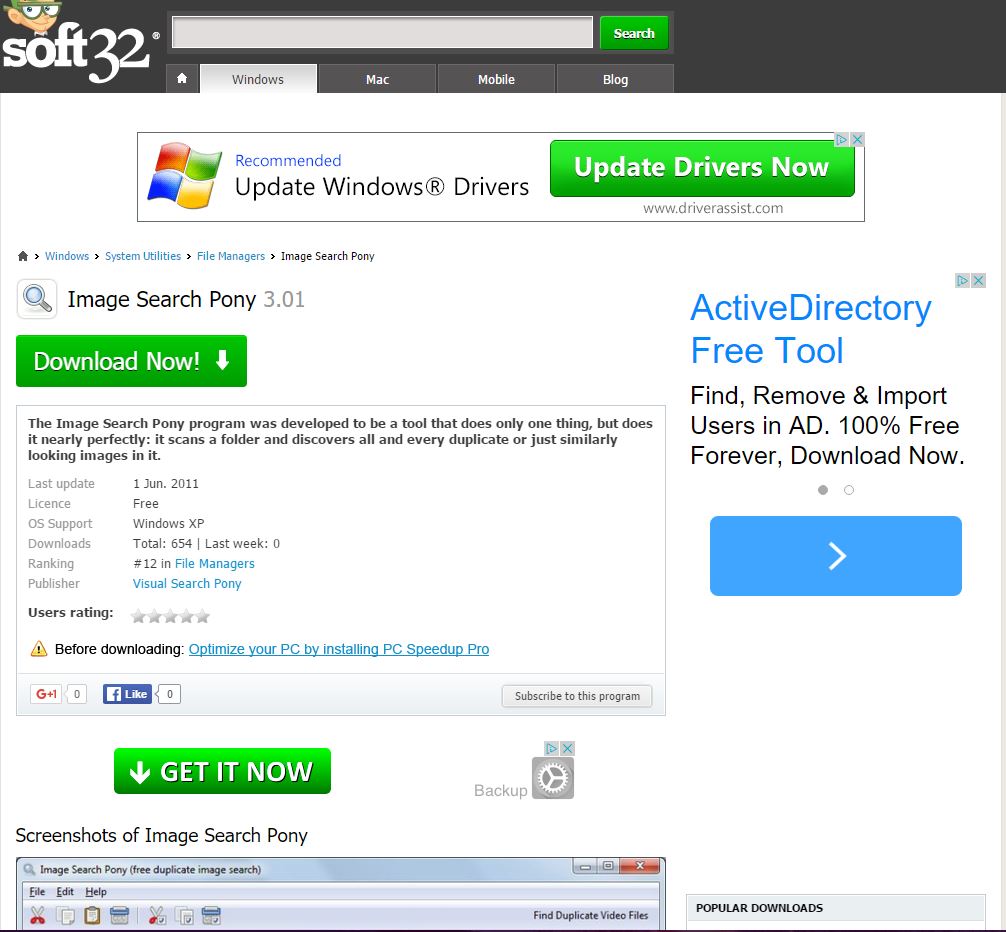
Safer downloading!
In my article on spring cleaning your computer I wanted to recommend tools which, while great in themselves, needed to be downloaded from freeware sites. The trouble is, these sites offer traps for the unwary. These safer downloading tips will help you use these sites with less risk. Trap 1: misleading search results Search for…
-

Creeper: the first virus
1971 saw the first computer virus—Creeper. It harmlessly copied itself and displayed the message “I’m the Creeper, catch me if you can!” Reaper swiftly followed. Its sole aim was to find and delete Creeper and was effectively the world’s first anti-virus. In the decade that followed, the few viruses created were simply experiments to push…
